When a Women's Safety App Becomes a Privacy Nightmare: Viral Tea App Data Breach
Key Takeaways
- Massive Exposure Goes Viral: 4chan users discovered and exploited an exposed Firebase database belonging to Tea, a popular women's safety dating app, accessing 72,000 images including selfies, driver's licenses, and private messages before sharing them publicly.
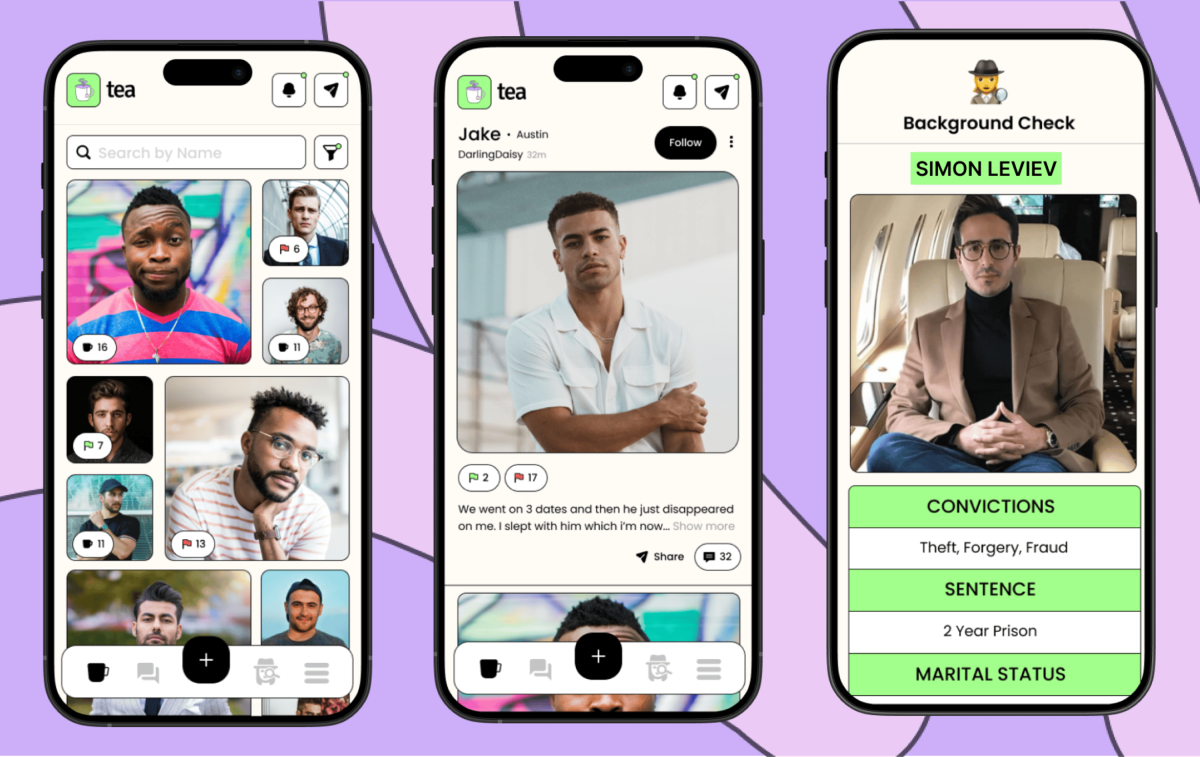
- The App Behind the Chaos: Tea is a women-only dating safety platform that lets users anonymously share experiences and warnings about men they've encountered, requiring selfie and ID verification for access. It exploded to #1 on the App Store this week with 1.6 million users seeking protection from bad dates.
- Security Through Obscurity Fails Spectacularly: The breach wasn't sophisticated hacking. It was a completely unsecured Google Firebase bucket that anyone could access, highlighting fundamental security architecture failures.
- Timing Couldn't Be Worse: The breach surfaced just as Tea hit #1 on the App Store with 1.6 million users, turning a moment of triumph into a privacy catastrophe for the very women the app promised to protect.
- Trust Destruction Is Immediate and Total: For an app built entirely on user trust and safety promises, this breach doesn't just compromise data. It obliterates the core value proposition and puts vulnerable users at serious risk.
Deep Dive
Tea, the viral women's safety app that surged to #1 on the App Store this week, promised women a safe space to share information about potentially dangerous dates. Instead, it became a playground for 4chan users to harvest and distribute the most sensitive personal data imaginable: selfies, driver's licenses, and private conversations from 72,000 users.
Here's what makes this breach particularly devastating: Tea required users to upload selfies and government IDs for "verification" purposes. The company claimed this was to ensure only women could access the platform. But these verification photos, along with private messages and posts, were stored in a completely unsecured Google Firebase database that anyone with the URL could access.
"Yes, if you sent Tea App your face and drivers license, they doxxed you publicly! No authentication, no nothing. It's a public bucket," read one 4chan post that included instructions for accessing the exposed data. "DRIVERS LICENSES AND FACE PICS! GET IN HERE BEFORE THEY SHUT IT DOWN!"
The timing makes this exponentially worse. Tea had just rocketed to the #1 spot on the Apple App Store this week, with tens of thousands of new users signing up daily. The app was experiencing massive viral growth precisely when its fundamental security failures were being exposed and exploited.
What's truly chilling is how quickly the exploitation escalated. 4chan users didn't just discover the vulnerability, they created automated scripts to mass-download personal data. Comments in the threads indicate thousands of images were harvested before the bucket was finally secured. The attackers specifically targeted the most sensitive verification photos, knowing these contained both faces and government identification.
404 Media confirmed the breach by decompiling the Android app and verifying the exposed Firebase URL matched what 4chan users were sharing. The vulnerability wasn't hidden deep in code, it was sitting in plain sight for anyone who bothered to look.
Tea's response raises additional red flags. The company initially claimed the exposed data was "from two years ago," as if that somehow diminishes the impact. Later statements revealed the breach included current user data after all. This kind of shifting narrative during crisis response suggests either poor incident management or an attempt to minimize the severity.
The broader implications are staggering. We're not talking about email addresses or phone numbers, this breach exposed the exact type of data that enables stalking, harassment, and identity theft. For women using an app specifically because they felt unsafe, this represents a complete betrayal of trust.
From a technical perspective, this breach should never have happened. Google Firebase provides robust security controls by default. Someone had to actively misconfigure the database to make it publicly accessible. This wasn't a sophisticated attack or zero-day exploit, it was basic negligence.
The legal ramifications will likely be severe. Tea collected highly sensitive verification data under the premise of user safety, then failed to implement even basic security controls. Class action lawsuits are virtually inevitable, and regulatory scrutiny will be intense.
The most heartbreaking aspect? Tea was actually trying to solve a real problem. Women face genuine safety concerns in online dating, and the app's core mission was admirable. But good intentions mean nothing when fundamental security practices are ignored.
The GRC Report is your premier destination for the latest in governance, risk, and compliance news. As your reliable source for comprehensive coverage, we ensure you stay informed and ready to navigate the dynamic landscape of GRC. Beyond being a news source, the GRC Report represents a thriving community of professionals who, like you, are dedicated to GRC excellence. Explore our insightful articles and breaking news, and actively participate in the conversation to enhance your GRC journey.
Sponsored by





.svg)

.svg)